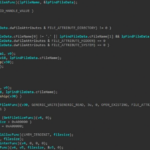
Best Practices and Risks Considerations in Automation like LCNC and RPA
By Jordan Bonagura Technologies such as Low-Code/No-Code (LCNC) and Robotic Process Automation (RPA) have become fundamental in the digital transformation of companies. …
Passive and Active Reconnaissance in Cybersecurity OSINT
Disclaimer: This is for educational purposes only. Among the key techniques used by cybersecurity professionals to understand and evaluate potential …
The Power of OSINT in Cyber Threat Intelligence
Disclaimer: This is for educational purposes only. In today’s interconnected world, cyber threats continue to grow in sophistication, frequency, and …
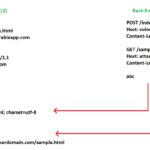
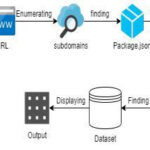
Uncovering Hidden Domains: A Guide to Subdomain Enumeration
Disclaimer: This is for educational purposes only. Subdomain enumeration is a foundational aspect of reconnaissance in cybersecurity, essential for penetration …

WiFi Deauthers vs Signal Jammers
The Theory behind WiFi Jamming in the RF Spectrum So what is a Jammer? How is a Deauther different? Overall, …
The Essential Guide to Radio Frequency Penetration Testing
Introduction What is Radio Frequency (RF)? Why is RF Pentesting Necessary? The Methodology Tools for RF Pentesting Common Vulnerabilities and …
Setting Up a Radio Frequency Penetration Testing Lab: A Comprehensive Guide
Introduction Understanding the Importance of Wireless Communication Security Defining Radio Frequencies Potential Security Threats Security Solutions What is Radio Frequency …
WIPER Malware
Nayana MG ABSTRACT: Cyber war is an emerging digital threat which sets its root firmly without even giving a chance …
API Penetration Testing: Tools, Techniques and Security Practices
Overview What is API Penetration Testing? How API Pen Testing Works Plan scope. This phase determines the testing methods and …
Passive and Active Reconnaissance in Cybersecurity OSINT
Disclaimer: This is for educational purposes only. Among the key techniques used by cybersecurity professionals to understand and evaluate potential …
Honeypot Technology: Comparisons, Types and Importance for Cyber Security
Honeypot technology holds significant importance in today's technology-driven world, serving as a crucial tool for safeguarding networks and monitoring evolving …
Hacking Drones with Flipper Zero: Exploring the Risks and Applications
The Flipper Zero, a multi-tool designed for hackers and security researchers, has proven to be a capable device for wireless …
Penetration Test Need-To-Know
What is a Penetration Test? A penetration test (also known as a pen test) is a simulated attack on an …
Best Practices and Risks Considerations in Automation like LCNC and RPA
By Jordan Bonagura Technologies such as Low-Code/No-Code (LCNC) and Robotic Process Automation (RPA) have become fundamental in the digital transformation of companies. …
Passive and Active Reconnaissance in Cybersecurity OSINT
Disclaimer: This is for educational purposes only. Among the key techniques used by cybersecurity professionals to understand and evaluate potential …
The Power of OSINT in Cyber Threat Intelligence
Disclaimer: This is for educational purposes only. In today’s interconnected world, cyber threats continue to grow in sophistication, frequency, and …
Uncovering Hidden Domains: A Guide to Subdomain Enumeration
Disclaimer: This is for educational purposes only. Subdomain enumeration is a foundational aspect of reconnaissance in cybersecurity, essential for penetration …

Aerial Assault: Combining Drones and Pentesting (W54)
Discover how to use drones for penetration testing with this innovative course. Gain skills in offensive and defensive drone operations, understand technical foundations, and learn about ethical and legal considerations. Perfect for cybersecurity professionals seeking to stay ahead in the field.
Aerospace Cybersecurity: Satellite Hacking (W53)
Dive into the essentials of satellite cybersecurity with this comprehensive course. Learn satellite reconnaissance, communication analysis, decoding techniques, and vulnerability assessments. Ideal for all skill levels, this course provides practical experience and theoretical knowledge, preparing you to protect satellite systems from cyber threats.
AutoSec Pro: Vehicle Cybersecurity Mastery (W52)
AutoSec Pro is an immersive course diving into the world of automotive cybersecurity, providing an in-depth understanding of modern vehicle systems and their vulnerabilities. This cutting-edge course leverages a hands-on approach to exploit and mitigate potential threats while seamlessly integrating the ISO 21434 standard. Harness the power of innovation and technology as you spearhead the effort to safeguard the future of smart transportation.
Creating Advanced Ransomware with Golang (W51)
In this course, you will develop a hybrid ransomware using, that is, with two encryptions RSA and AES with a programming language that is gaining a lot of strength - Golang