Authors
Pranali Phadtare, Soummya Kulkarni, Shruthi Shunmugom M
About Us
IBM PTC is a proficient internal Security Test Team responsible for vulnerability assessment & ethical
hacking of web, mobile applications & infrastructure.
Abstract
HTTP/2 is an upgraded version of the HTTP 1.1 protocol. HTTP/2 provides various considerable refinements in terms of performance by addressing the prominent issues with HTTP/1.1 protocol. These refinements seems to have incidental impact in terms of security. This article tries to elucidate various functionalities of HTTP/2 and also explains web application related vulnerabilities of HTTP/2, such as Denial of Service attacks and downgrading vulnerabilities.
Introduction to HTTP Protocol
HyperText Transfer Protocol (HTTP) is a communication protocol used to connect to Web servers on the Internet or on a local network. The primary function of HTTP is to establish a connection with the server and send HTML pages back to the user's browser. It is also used to download data from the server, either to the browser or to any requesting application that uses HTTP.
HTTP is an application layer protocol and works on Client-Server model. Basic working of HTTP can be as follows:
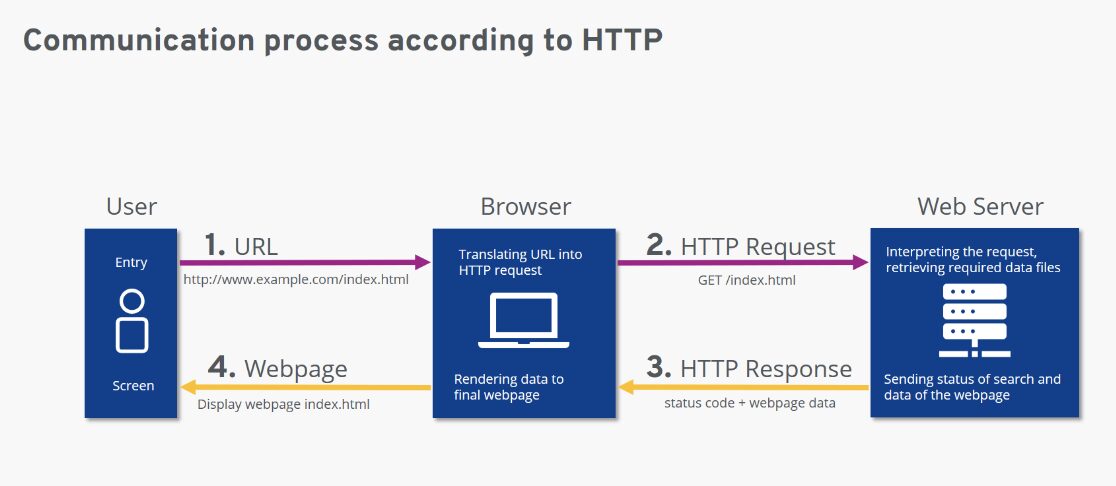
- Client establishes TCP connection with server.
- Client sends an HTTP request to server....
