
INTRODUCTION TO PENETRATION TESTING
Penetration Testing is used to evaluate a computer system’s security by performing authorized simulated attacks. A cybersecurity expert performs penetration testing to identify vulnerabilities and weak spots in a system’s security which hackers or attackers could exploit. A penetration test is also known as pen test and, a penetration tester is called an ethical hacker.
Benefits of Penetration Testing:
- Identification and Remediation of weaknesses in systems
- Ensure compliance with data privacy and other regulatory requirements
- Enhance customer trust
- Ensure Business Continuity
Overview of Penetration Testing Methodologies:
Some of the most common methodologies of Penetration Testing are listed below:
- Open-Source Security Testing Methodology Manual (OSSTMM)
- Open Web Application Security Project (OWASP)
- National Institute of Standards and Technology (NIST)
- Penetration Testing Execution Standards (PTES)
- The Information System Security Assessment Framework (ISSAF)
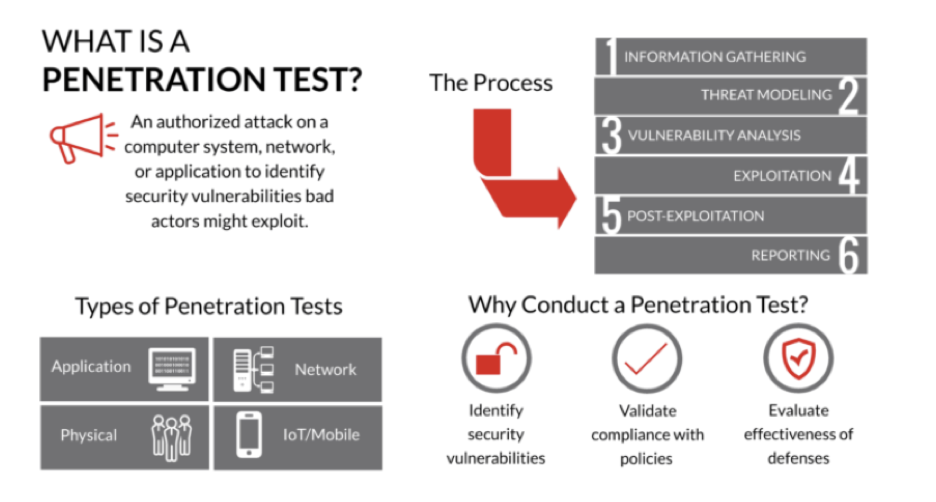
(Image Source : https://plextrac.com/what-is-a-penetration-test/ )
IMPORTANCE OF HAVING A PENETRATION TESTING LAB
Penetration Testing involves accessing computer systems for vulnerabilities which, can pose a risk if conducted on live production systems. A penetration testing lab ensures that the testing activities do not affect the real-world operations and they take place in a controlled environment.
It is illegal to carry out testing on live systems without proper authorization. An ethical lab allows professionals to conduct....
